Highlights
Narrowing the gap between theory and practice for quantum secure communications
 A team led by CQT Principal Investigator Charles Lim developed a new optical device known as a power limiter that defends QKD systems against side-channel attacks. From left, NUS Research Fellows Zhang Gong and Wang Chao with the team’s power limiter.
A team led by CQT Principal Investigator Charles Lim developed a new optical device known as a power limiter that defends QKD systems against side-channel attacks. From left, NUS Research Fellows Zhang Gong and Wang Chao with the team’s power limiter.
Researchers from CQT and their collaborators have developed two methods, one theoretical and one experimental, to protect the security of quantum key distribution (QKD), a technology that can be deployed in any communication network that needs long-term security. The first is a twist on the ultra-secure cryptography protocol known as ‘device-independent’ QKD (DIQKD). The second is a first-of-its-kind device that defends QKD systems against bright light pulse attacks by creating a power threshold.
QKD is a method for secure communication that uses quantum mechanics to encrypt information. While the security of QKD is unbreakable in principle, if it is incorrectly implemented, vital information could still be stolen by attackers. These are known as side-channel attacks, where the attackers exploit weaknesses in the setup of the information system to eavesdrop on the exchange of secret keys. The two new methods proposed ensure that QKD communications cannot be attacked in this way.
“Rapid advances in quantum computing and algorithmic research mean we can no longer take today’s toughest security software for granted. Our two new approaches hold promise to ensuring that the information systems which we use for banking, health and other critical infrastructure and data storage can hold up any potential future attacks,” said CQT Principal Investigator Charles Lim, who led the two research projects. Charles holds a joint appointment as Assistant Professor in the NUS Department of Electrical and Computer Engineering.
Future-proof quantum communication protocol
Critically, the security of DIQKD can be checked without needing to characterise the quantum devices used. Typically, in QKD, quantum devices perform measurements using two measurement settings – one to make a secret key and another to test the integrity of the channel.
In a paper published in Nature Communications on 17 May 2021, the team showed that with their new DIQKD protocol, users can independently test the other party’s encryption device by generating a secret key from two randomly chosen key generation settings instead of one. The researchers demonstrated that introducing an extra set of key-generating measurement for the users makes it harder for the eavesdropper to steal information.
“It’s a simple variation of the original protocol that started this field, but it can only be tackled now thanks to significant developments in mathematical tools,” says CQT Principal Investigator Valerio Scarani, who was one of the inventors of this type of method and is a co-author on the paper. Besides Charles, the other co-authors are René Schwonnek and Goh Koon Tong from NUS, Ignatius William Primaatmaja from CQT, Ernest Tan from ETH Zürich and Ramona Wolf from Leibniz Universität Hannover.
Compared to the original DIQKD protocol, the new protocol is easier to set up, and is more tolerant to noise and loss. It also gives users the highest level of security allowable by quantum communications and empowers them to independently verify their own key generation devices.
With the team’s setup, all information systems built with DIQKD would be free from misconfiguration and mis-implementation. “Our method allows data to be safe against attackers even if they have unlimited quantum computing power. This approach could lead to a truly secure information system, eliminating all side-channel attacks and allowing end-users to monitor its implementation security easily and with confidence,” explained Charles.
A first-of-its-kind quantum power limiter device
Quantum cryptography, in practice, uses optical pulses with very low light intensity to exchange data over untrusted networks. Leveraging quantum effects can securely distribute secret keys, generate truly random numbers, and even create banknotes that are mathematically unforgeable.
However, experiments have shown that it is possible to inject bright light pulses into the quantum cryptosystem to break its security. This side-channel attack strategy exploits the way injected bright light is reflected to the outside environment, to reveal the secrets being kept in the quantum cryptosystem.
In a new paper published in PRX Quantum on 7 July 2021, the researchers from CQT and NUS reported their development of the first optical device to address the issue. Zhang Gong, Wang Chao, Haw Jing Yan and Gong Xiao from the NUS Department of Electrical and Computer Engineering worked on this project with Charles and Ignatius.
The optical device is based on thermo-optical defocusing effects to limit the energy of the incoming light. The researchers use the fact that the energy of the bright light changes the refractive index of the transparent plastic material embedded in the device, thus it sends a fraction of the light out of the quantum channel. This enforces a power limiting threshold.
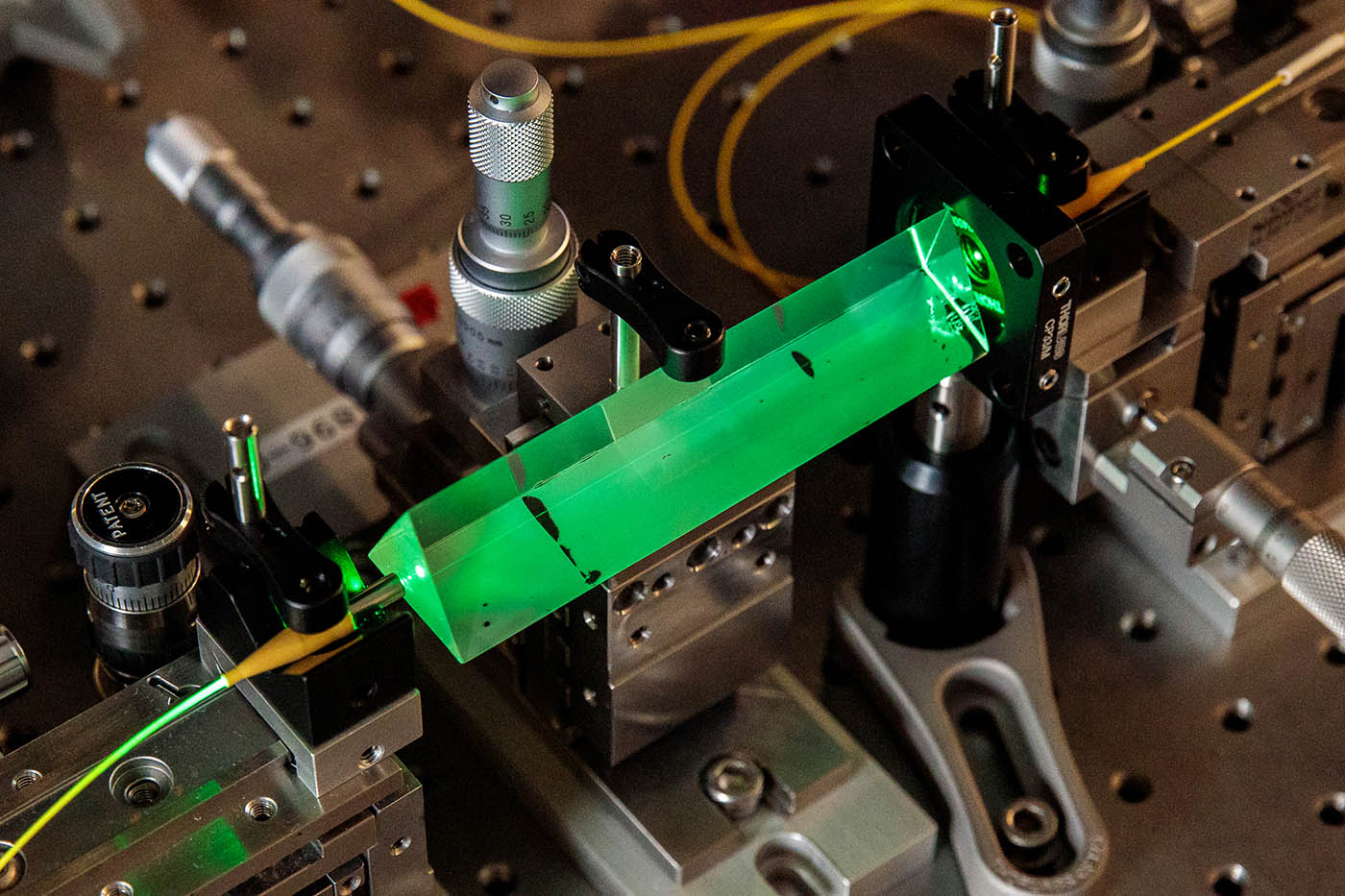 The most important component of the team’s power limiter is this acrylic prism measuring about 10cm in length. It works like a fuse to send a fraction of the incoming bright light out of the quantum channel.
The most important component of the team’s power limiter is this acrylic prism measuring about 10cm in length. It works like a fuse to send a fraction of the incoming bright light out of the quantum channel.
The team’s power limiter can be seen as an optical equivalent of an electric fuse, except that it is reversible and does not burn when the energy threshold is breached. It is highly cost-effective, and can be easily manufactured with off-the-shelf components. It also does not require any power, so it can be easily added to any quantum cryptography system to strengthen its implementation security.
Charles added, “It is imperative to close the gap between the theory and practice of quantum secure communications if we are to use it for the future Quantum Internet. We do this holistically – on one hand we design more practical quantum protocols and on the other hand, we engineer quantum devices that conform closely with the mathematical models assumed by the protocols. In doing so, we can significantly narrow the gap.”
This text is adapted from a press release by NUS.
On 6 July 2021, Charles and Wang Chao gave their views in Nature Photonics on the recent twin-field QKD demonstration over 511 km of optical fibre by researchers in China. They also identified future research directions in the article. The piece can be read here: https://rdcu.be/cnR1S